Chakib Jaber
Chief Technology Officer
SpinSys
In 2014, DIACAP was scheduled to be replaced by the Risk Management Framework, or RMF, for DoD Information Technology. Understanding the distinctions between frameworks is critical for organizations that work with government information systems.
DIACAP Essentials
The DIACAP Process was initially formulated as a part of an effort to improve the continuous management of IA. It instituted a rigorous process for how information systems could be certified for their adherence to DoD security guidelines. It also included standards for accrediting such systems for operation by specific officials.
To maintain compliance, a given system had to provide for five central activities, namely:
- Initiating and planning IA certification and accreditation, or C&A,
- Implementing and validating the assigned IA controls derived in the previous step,
- Making certification determinations and accreditation decisions,
- Maintaining authorization for operating and conducting reviews, and
- Decommissioning or retiring a certified system.
Along with performing the above activities, information systems that satisfied DIACAP governance rules generated five major artifacts. These were:
- System Identification Profiles created when the system was registered,
- DIACAP Implementation Plans that included implementation strategies and information about assigned controls,
- Supporting Documentation for Certification records that held the results of control validation,
- DIACAP Scorecards that rated information systems on their compliance, and
- Plan of Action & Milestones tools that addressed how vulnerabilities would be remedied.
The DIACAP process nominated Certification Authorities, or CAs, who evaluated proposed IA implementations and potential risk factors based on their severity. Designated Approval Authorities, or DAAs, would then make accreditation decisions to determine how systems could operate. Reviews were implemented at least annually.
Transitioning to RMF
Just as DIACAP improved on some of the standards of earlier guidelines like DITSCAP, or the Defense Information Technology Security Certification and Accreditation Process, RMF expands on DIACAP’s scope. The new standard is applicable not only within the DoD but among all Federal government agencies.
One of the key philosophical improvements is that RMF focuses heavily on managing organizational risk. In addition to accounting for hazards that directly impact IA processes and information systems, the framework also addresses risks that affect individuals or organizations. This is vital because these organizational elements may act as weak points or expose vulnerabilities.
RMF also incorporates a number of important practical differences. These include:
New Authorization Decision-Making Processes
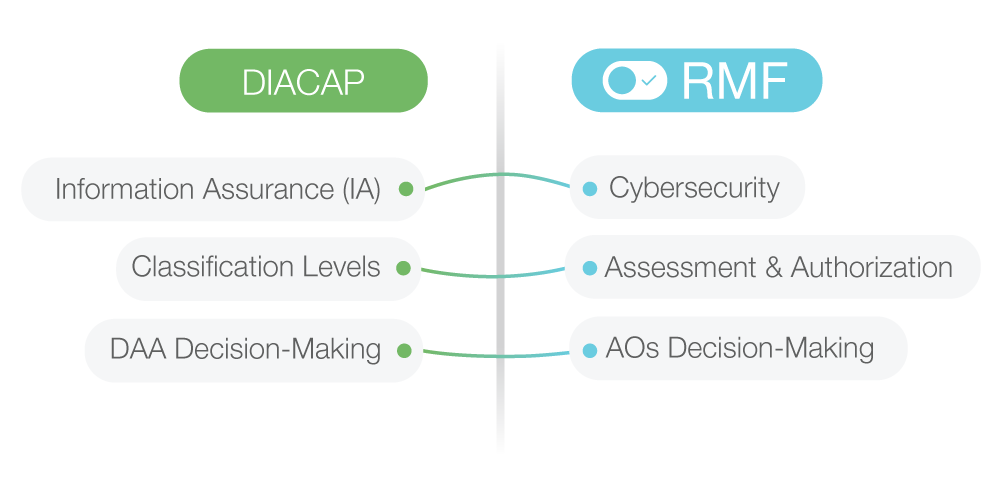
DIACAP authorized a sole DAA to make authorization decisions for each system under evaluation. RMF replaces DAAs with authorizing officials, or AOs, who can provide authorization in a joint fashion. It’s easy to see how such changes might result in more effective oversight.
RMF also restructures one of DIACAP’s authorization statuses to eliminate the risk of lasting weaknesses. DIACAP employed a status called Interim Authority to Operate, or IATO, that allowed systems to operate while managing their known IA vulnerabilities for up to six months. The new framework replaces this with conditional Authority to Operate, or ATO, designations that permit restricted functionality. It also mandates that subsequent authorizations have to come from higher-level decision makers following two conditional ATOs.
Changing Classification Levels
DIACAP employed Mission Assurance Category, or MAC, levels I, II and III to rank the importance of individual systems. It also categorized systems by Classification Level, or CL, designations known as Classified, Sensitive and Public. RMF replaced the MAC structure with Low, Moderate and High Impact Levels and supplanted CLs with three Security Objectives.
There’s some correlation between the old MAC levels and the RMF Impact Levels. The new Security Objectives, however, aren’t 100 percent congruent with the prior standards. For instance, a given system may receive an independent evaluation and distinct rating for the different Security Objective areas, or Availability, Integrity and Confidentiality. It’s critical to understand how these differences affect systems and their stakeholders.
RMF uses an Assessment & Authorization, or A&A, process instead of the C&A process familiar to most DIACAP users. While there are numerous salient differences, one overarching theme is that A&A focuses on security far earlier in the process.
How Will Tomorrow’s Leaders Keep up With RMF?
The preceding differences only address a limited number of the disparities between DIACAP and RMF. For instance, many of the job titles and vocabulary terms common to DIACAP were redefined or renamed in RMF. This can make the transition process confusing to those who simply try to realign their old compliance standards with new frameworks.
The Six Steps to Applying RMF to Federal Government Systems
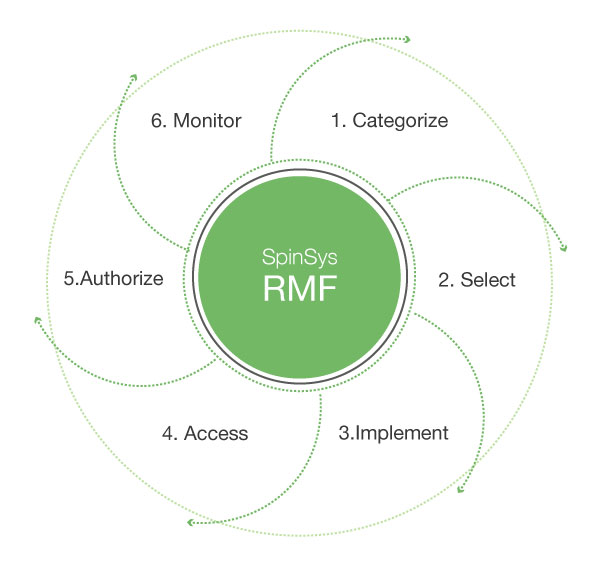
Fortunately, the National Institute of Standards and Technology, or NIST, Computer Security Division lays out in clear terms how organizations should properly implement RMF. There are six general steps organizations need to adhere to:
- Categorize: Information systems and any data they process, store or transmit should be categorized according to an impact analysis.
- Select: Baseline IA controls must be selected in accordance with the categorizations devised in the previous step, organizational risk assessments and other factors.
- Implement: The IA controls should be implemented and have their deployment documented appropriately.
- Assess: The implemented controls should be accurately assessed to determine their efficacy and outcome within the context of the system’s security requirements.
- Authorize: The information system’s operation needs to be authorized considering known and acceptable risks to assets, individuals and national security.
- Monitor: The IA controls should be continually monitored and evaluated. This also includes rigorous change documentation, routine reporting to authority figures and security-impact analyses of modifications.
Beginning an Effective Transition
RMF shares many goals with earlier frameworks like DIACAP, but the differences between the standards are extremely important. So is the new mindset that entities must adopt to implement and maintain effective governance practices.
Switching to RMF requires a wholly different approach to cybersecurity and risk assessment. Factors like transparency, reciprocity and continuity are of heightened importance in the modern world, and standards are evolving to reflect such changes. To meet these demands, contemporary security risk management must be instituted at organizational and systemic levels alike.
Government agencies, private-sector companies and other organizations utilize information-system technologies in unique ways. Going forward, these entities will need to adopt comprehensive compliance methodologies to succeed in domains like training, leadership and systems engineering. To learn more about incorporating RMF into your mission plan, visit us at SpinSys.com.